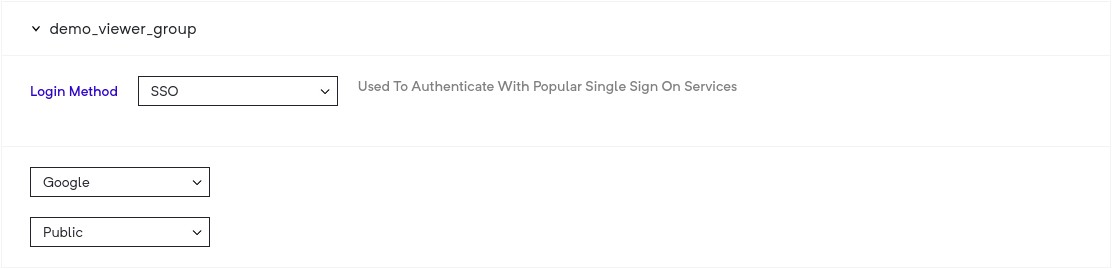
SSO
This option allows you select either Google, Microsoft (Azure) or SAML based login for viewers.
Google and Microsoft Azure based SSO
When you use this, you have three options:
Public - all people with valid (google or azure based on your selection) accounts are allowed to access your deployment.)
Filter By domain - all people with valid google or azure based accounts on the domain that you have set are allowed to access your deployment.
Filter By viewer list - all accounts google or azure based accounts in your viewer list are allowed to access your deployment.
SAML based SSO
This is a viewer group authentication mechanisms support for the Security Assertion Markup Language.
Identity Provider Setup
Any SAML identity provider (IdP) can be configured to be used for authentication of a viewer.
To enable this, head over to the Viewer Group page, then:
Select SSO as your
Login Method.Now select
SAMLfrom theProviderdrop-down menu.After this, you will be asked to provide your SAML IdP configuration.
You should see the config as follows:
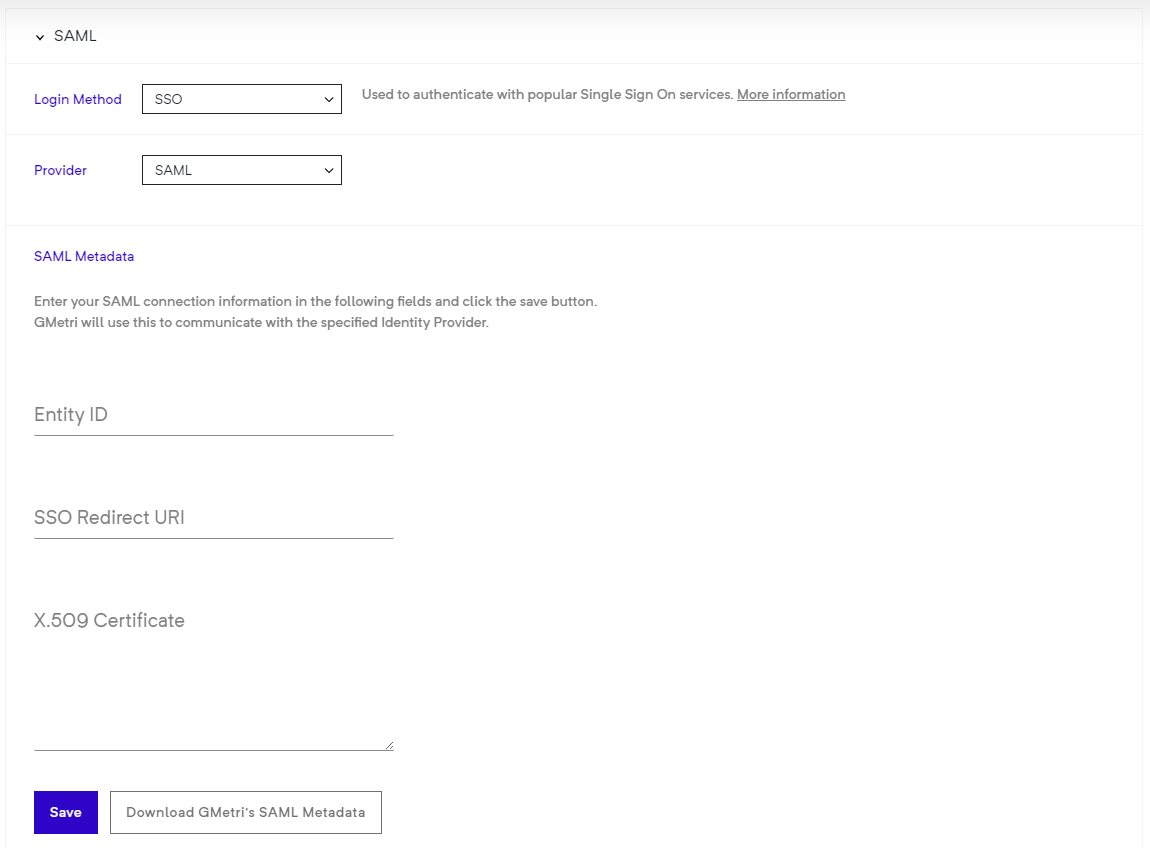
Enter your IdP's
entityId,SSO redicrection URLandX.509 signing certificate.Click the
Savebutton to finally save your configuration.To register GMetri as a service provider (SP) with your IdP, you will need the configuration details. You can get these details by clicking the
Download GMetri's SAML Metadatabutton.
You can find sample metadata configuration here under the SAMLtest's IdP section. This will give you an idea of what you need to paste in the boxes for the SAML config.
NOTE on pasting X.509 certificate
Please paste certificate without the ----BEGIN CERTIFICATE---- and ----END CERTIFICATE---- part.
Deployment Setup
Once you create a SAML viewer group, head to your deployment and set this viewer group as the authentication mechanism for that deployment.
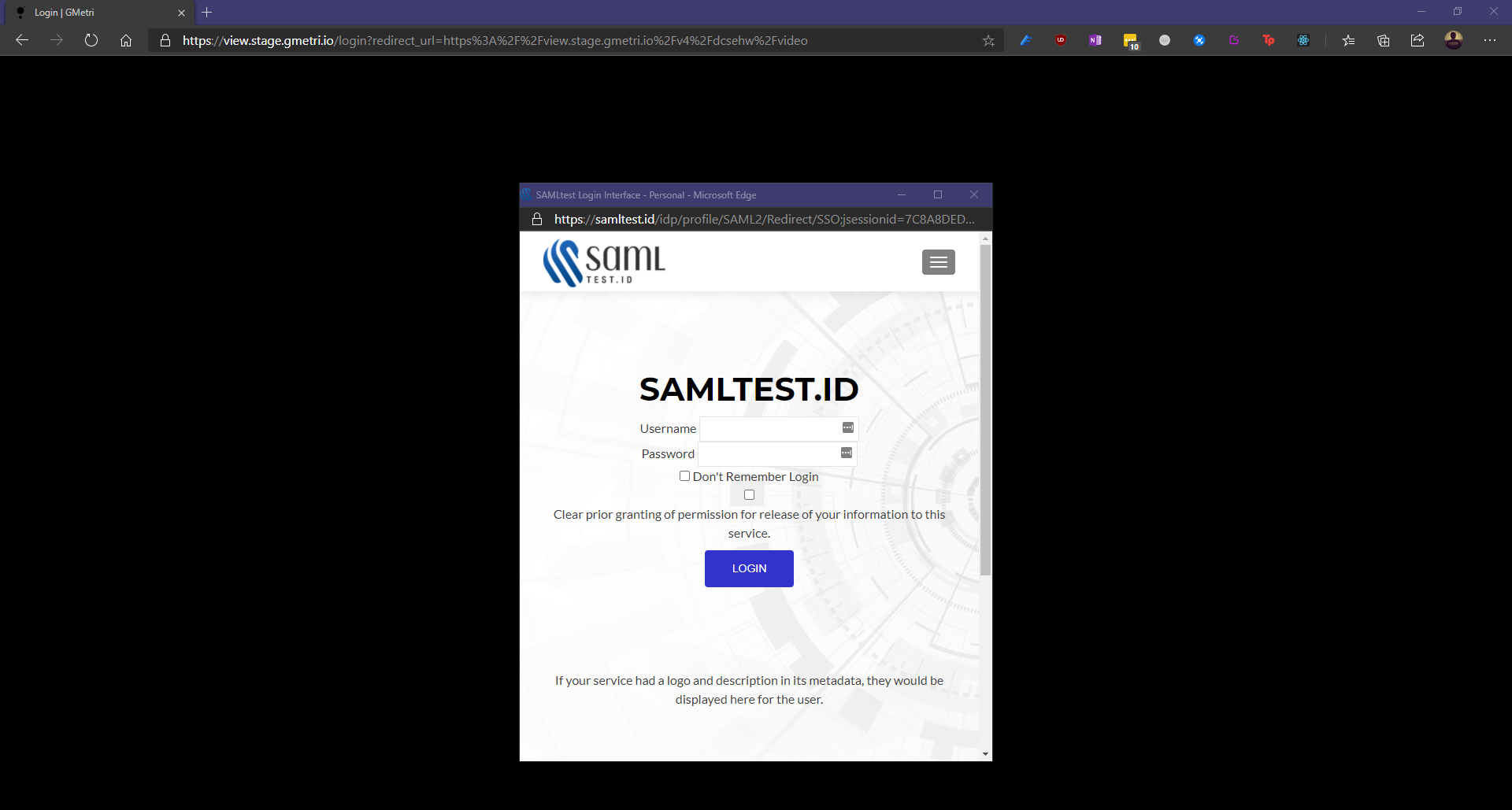
Viewer
Once you open a viewer link for deployment with a SAML SSO based viewer group, you will see a pop-up with the IdP's login page.
Post-IdP login process, you will be redirected back to
view.gmetri.com.We use your
email addresssent to us by theIdPas the primary identifier for the viewer session.
SAML configuration
Name Identifier format:
urn:oasis:names:tc:SAML:1.1:nameid-format:unspecifiedIn IdP
SAMLResponsewe look for the following attributes:
email/mail
urn:oasis:names:tc:SAML:2.0:attrname-format:uri
Display Name
displayname / urn:oid:2.16.840.1.113730.3.1.241
urn:oasis:names:tc:SAML:2.0:attrname-format:uri
SAML authentication will not be successful unless the IdP returns your email in its SAML response.
Last updated
Was this helpful?

